Τελευταία επεξεργασία από: thanasis, 10/10/2009 - 03:19
ChronicdevTeam's GreenPois0n
Από
hostolis
, 12/09/2009 12:30
50 μηνύματα σε αυτό το θέμα
#46

Δημοσίευση 29/09/2009 - 21:59
Αντε γιατι εχω αρχισει να βλεπω στον υπνο μου τα 3GS να χοροπηδανε γυρο μου σαν κατσικια!!!! 


Ad
#47

Δημοσίευση 02/10/2009 - 20:32
Another Progress Update
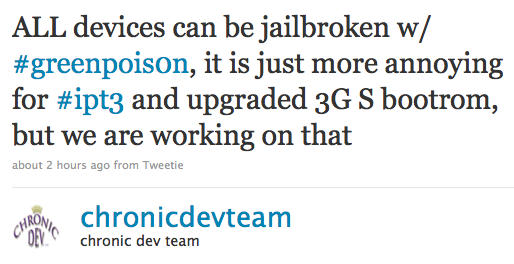
Because so many people on Twitter and the comments want an update, here it is. We said it would be technical, so please don’t get pissed off if you don’t understand it and do not flood the comments with questions of “what does this mean?”.
- After a stupid mistake was corrected, posixninja was able to use a payload written by ius that retrieved the location of the aes_crypto_cmd routine, so now we can decrypt the firmware files.
- “greenpois0n”, as in, the payload, is coming along quite nicely. This is it’s third rewrite, and I am doing it entirely in C with the exception of the loader.
Plans for the end product
- No DFU required
- No extra time to send over a ramdisk and boot that, everything is planned to be done over iBoot
- No IPSW required, firmware files are read directly from flash, then decrypted and patched on the fly, then reflashed and / or put aside to be booted from later
- If the device is connected in Normal Mode, automatically reboot into Recovery Mode
- Jailbreak takes less than 1 minute from the time it boots to recovery
- Verbose reporting of progress, like “patching iBoot” or “reflashing DeviceTree” on the screen of the device, if you don’t understand what this means, it is similar to what the screen looks like if you were verbose booting your Mac / iPhone
- Extra patches such as access to the UID and GID keys from userland automatically applied, no need to dig up kernel decryption keys and use the patcher provided in xpwn and such
- Totally untethered jailbreak. This may or may not require an extra exploit.
- In case our exploit is in any other firmware revision, it can be ported in just a few line changes.
If you did not understand what some of that meant, this is the most important fact: on release, you will be able to go up to some random laptop at Best Buy, download the very small program plug in your device no matter what state it is in (normal or recovery), run it, and 1 minute later your device will be jailbroken. I am obviously not suggesting you randomly go in and do that, but the point I am trying to get across is that you will not need to prerequisites like libUSB, just plug it in, push a button, and the jailbreak is done in 1 minute. This is the way jailbreaking should always be.
[Via chronic-dev.org]
Because so many people on Twitter and the comments want an update, here it is. We said it would be technical, so please don’t get pissed off if you don’t understand it and do not flood the comments with questions of “what does this mean?”.
- After a stupid mistake was corrected, posixninja was able to use a payload written by ius that retrieved the location of the aes_crypto_cmd routine, so now we can decrypt the firmware files.
- “greenpois0n”, as in, the payload, is coming along quite nicely. This is it’s third rewrite, and I am doing it entirely in C with the exception of the loader.
Plans for the end product
- No DFU required
- No extra time to send over a ramdisk and boot that, everything is planned to be done over iBoot
- No IPSW required, firmware files are read directly from flash, then decrypted and patched on the fly, then reflashed and / or put aside to be booted from later
- If the device is connected in Normal Mode, automatically reboot into Recovery Mode
- Jailbreak takes less than 1 minute from the time it boots to recovery
- Verbose reporting of progress, like “patching iBoot” or “reflashing DeviceTree” on the screen of the device, if you don’t understand what this means, it is similar to what the screen looks like if you were verbose booting your Mac / iPhone
- Extra patches such as access to the UID and GID keys from userland automatically applied, no need to dig up kernel decryption keys and use the patcher provided in xpwn and such
- Totally untethered jailbreak. This may or may not require an extra exploit.
- In case our exploit is in any other firmware revision, it can be ported in just a few line changes.
If you did not understand what some of that meant, this is the most important fact: on release, you will be able to go up to some random laptop at Best Buy, download the very small program plug in your device no matter what state it is in (normal or recovery), run it, and 1 minute later your device will be jailbroken. I am obviously not suggesting you randomly go in and do that, but the point I am trying to get across is that you will not need to prerequisites like libUSB, just plug it in, push a button, and the jailbreak is done in 1 minute. This is the way jailbreaking should always be.
[Via chronic-dev.org]
#49

Δημοσίευση 10/10/2009 - 01:41
για unlock δεν λεει ομως και.... λυπαμαι αλλα δεν μας κανει 
Χρήστες που διαβάζουν αυτό το θέμα: 1
0 μέλη, 1 επισκέπτες, 0 ανώνυμοι χρήστες