Ο Sauric συμμετείχε στο Live Chat του TUAW και απάντησε σε ερωτήσεις σχετικά με το φλέγον θέμα του Jailbreak και του νέου signature server της Apple.
Η συζήτηση είναι πραγματικά πολύ ενδιαφέρουσα και θα σας λύσει τυχόν απορίες σχετικά με αρκετούς από τους όρους που ακούτε το τελευταίο διάστημα (ECID, IBSS, IBEC κ.α):
|
4:13
|
Erica: Hi everyone. We’re still getting set up and we’ll start in just a few minutes. |
|
4:16
|
Erica: And I think we’re good to go. |
|
4:17
|
Erica: I want to welcome everybody to our chat today. Today, we have the pleasure of talking with Jay Freeman. You might know him better as “saurik”. He is the developer of Cydia and the godfather of the jailbreak world. |
|
4:17
|
Jay Freeman (saurik): Hello! |
|
4:17
|
Erica: We have several TUAWians who will be hopefully showing up to join in the chat as well. In addition to me, we should be seeing Mike Jones, Megan Lavey, and Josh Carr |
|
4:18
|
Megan Lavey: I’m here! Good afternoon, Erica and Jay! |
|
4:18
|
Michael Jones: Good afternoon everyone! |
|
4:18
|
Erica: The big motivating factor for today’s chat is Apple’s new signing server. Jay, can you offer a brief overview of what it is, and what it means to iPhone users? |
| 4:19 |
Have you jailbroken?
You bet! ( 82% )
Thinking about it… ( 4% )
Not yet ( 3% )
Haven’t and don’t plan to ( 8% )
Isn’t that against the law? ( 1% )
|
|
4:19
|
Jay Freeman (saurik): Gladly. In order for things like jailbreaking to work (or any homebrew development in a hostile environment), bugs need to be found and exploited in the software that runs on the device. |
|
4:20
|
Jay Freeman (saurik): Unfortunately, hackers tend to have the fundamental advantage in such wars: software is released, and it must “stand the test of time”: users may choose to simply never update their devices, and wait for exploits to be uncovered. |
|
4:21
|
Jay Freeman (saurik): Apple’s response to this problem has been to make their new devices, the 3G[S] and the craazy new iPod (the larger sizes of the third generation iPod Touch), verify that, when the device is “restored” (when it is erased and the software is put back onto it) that software is considered “secure”. |
|
4:22
|
Jay Freeman (saurik): This happens by having iTunes contact the Apple firmware signature server, gs.apple.com, sending it information about the device in question and the software that you are trying to load. In fact, every single individual file being sent to the device goes through this process (although one request to Apple’s server can ask for multiple signatures at once). |
|
4:23
|
Jay Freeman (saurik): So, to answer the question that some people have been asking in the “comments” section of this chat: yes, in order to restore your new i-devices, you will need to have an internet connection at the time of the restoration. |
|
4:24
|
Jay Freeman (saurik): The device then has algorithms in it to verify the validity of that signature. |
|
4:25
|
Jay Freeman (saurik): However, the way Apple implemented this allows for something called a “replay attack”: where you take a recording of Apple signing the software, and then “reply” that process to the device, which gets confused and accepts the signature. Nothing about the process includes, for example, the current time, which could be used to verify “is this an original, or a recording”. |
|
4:26
|
Erica: Apple has always been proprietary about controlling the iPhone family of devices. How does this new step compare to previous moves on Apple’s part, and how does it affect people who want to downgrade or jailbreak? And, is there any legal or ethical questions about your replay attack approach? |
|
4:28
|
Jay Freeman (saurik): This next step is right in line with that their previous work in this area, and is in essence the next logical step to protecting the device. This method should, were it implemented correctly, keep users from not only downgrading their device to older firmwares but also keep users from being able to maintain a device on an older version by simply never upgrading: if anything happens to the device and the software has to be reloaded, for any reason, the user will be forced to use currently “ok” versions of the firmware. |
|
4:29
|
Jay Freeman (saurik): To answer the question about “legal or ethical questions” about the replay attack, I will first state that I am not a lawyer, but will say that I do not believe there to be any issues regarding this technique. |
|
4:30
|
Erica: I understand that you have set up a server that mimics Apple’s. Can you tell us more about this? |
|
4:32
|
Jay Freeman (saurik): There is a specific “protocol” (the description of the interactions and what is allowed to be said back/forth) used between iTunes and Apple’s signature server to ask “is this file ok”. This protocol is neither encrypted nor obfuscated in any manner: it is actually entirely transparent to people trying to understand it. |
|
4:34
|
Jay Freeman (saurik): (For any techno-geeks out there: Apple sends an XML “plist” formatted Property List to the server including base64 digests of hashes of parts of the file, as well as the chip/board identifiers that determine what kind of device it is, and finally the per-device ECID: the server then returns a plist of signatures.) |
|
4:34
|
Erica: Can you tell us more about the ECID SHSH? What is the ECID and is Apple tracking their users here a little too closely for comfort? |
|
4:36
|
Jay Freeman (saurik): The ECID is also known as the “unique-chip-id”, and all of these smarter i-devices include one. I am actually not certain of its entire purpose, but I currently do not know of any other usage of the identifier than this signature process on the 3G[S] and the craazy new iPod. |
|
4:37
|
Jay Freeman (saurik): The SHSH’s that people speak of are the signature hashes returned by the server. There is one SHSH per ECID/file pair (and there are some 17 files that make up a build of Apple’s firmwares). |
|
4:37
|
Erica: Apparently there was a period of just a few hours when you started registering ECIDs for Cydia users, so they could perform indefinite restores to 3.0. How did this work, and why did things time out? |
|
4:37
|
[Comment From Will] Is there an easy way for users to retrieve their own ecid shsh for safe keeping |
|
4:38
|
Michael Jones: Good question Will. |
|
4:38
|
Jay Freeman (saurik): I had been working for a while on the details of how to get the ECID off the device from a normal program (such as Cydia): while not at all hard in the end, previously people had only been getting it by putting the device into recovery mode (where you are going to plug the device into iTunes to fix it) and using a USB viewer. |
|
4:39
|
Jay Freeman (saurik): I finally managed to get the time required to get this into a build of Cydia days before the 3.1 version of the firmware came out. |
|
4:40
|
Erica: So what you’re storing isn’t just the ECID but the ECID and the signature hash for those 7 or so files? Does knowing the ECID alone get you anything? |
|
4:40
|
Jay Freeman (saurik): Unfortunately, when the 3.1 firmware came out (which fixed the bug used by purplera1n and redsn0w 0.8), Apple wisely and, as expected, stopped signing the files from the 3.0 firmware. |
|
4:41
|
[Comment From James Tanner] @will – TinyTSS includes a program called Umbrella which will get your 3.1 shsh file, and is you modify the hosts as per Sauriks link, you can also get your 3.0 shsh (assuming you made it in time) from Sauriks server (sorry, i dont want to push light away from Saurik etc but its worth noting) |
|
4:42
|
Jay Freeman (saurik): Correct: my server is storing, pretty much, ECID+ChipID+BoardID+”File” -> SHSH. I am nearing 3 million of these entries stored. I then use these records to reconstruct the response from Apple’s signature server. |
| 4:43 |
How long has your iPhone or iPod been jailbroken?
Since the beginning ( 53% )
After the really easy 1.1.3 j/b ( 8% )
When the 3G debuted ( 13% )
Within the last 6 months ( 14% )
Haven’t j/b ( 12% )
|
|
4:43
|
Jay Freeman (saurik): Users who want to get this information from either my server or Apple’s server need only make a standard Apple signature server request: if the firmware is “current” they can get it from Apple, and if not they will need to get it from me (if I have it stored, of course). |
|
4:44
|
Erica: Do you have any tools right now for people to use on their non-jailbroken units? Through Ad-hoc or self-signing? |
|
4:44
|
Jay Freeman (saurik): I will be offering a mechanism for users to do this more easily in the future, but for right now users who wish to do this can do so using the following Python program:
http://svn.saurik.com/repos/menes/trunk/cysts/tss.py |
|
4:45
|
Erica: It would be great if people could grab their hashes and their IDs and submit it to your sever. |
|
4:45
|
Jay Freeman (saurik): For non-jailbroken units the easiest thing to do at this time is to switch to using my signature server replacement and then to do a restore. |
|
4:46
|
Erica: So what I’d do is edit my /etc/hosts file to point to 74.208.105.171 gs.apple.com, yes? |
|
4:46
|
Erica: And then launch iTunes and restore a 3GS or 3rd gen iPod touch? |
|
4:46
|
Jay Freeman (saurik): Correct. On a Windows machine one would use C:\Windows\System32\drivers\etc\hosts to do the same thing (I hope I got that path right ;P). |
|
4:46
|
Erica: Should users of earlier gen devices even bother or worry? |
|
4:47
|
Jay Freeman (saurik): I am not certain at this time. I have noticed some requests going through for second generation iPod Touches, but I have not had time yet to figure out why. |
|
4:49
|
Jay Freeman (saurik): I am noticing some questions I get a lot in the “Recent Comments” section. |
|
4:49
|
Erica: Have you heard any reports of people being unable to install jailbroken firmware on newer devices? And how does this affect people who bought their 3GS units with 3.1 already installed? |
|
4:50
|
Jay Freeman (saurik): To Liam: When I say 3G[S] I mean specifically the new device, not the older 3G. The brackets around the S are my way of rendering the square that Apple puts around the S: “3GS” is not a correct moniker for the device. |
|
4:50
|
Erica: Jay, click on any of the questions you want to answer and they’ll show up in the chat |
|
4:50
|
[Comment From Liam] So, when you said 3G[S], did you mean just the 3GS, or 3G and 3GS are protected in this way? |
|
4:52
|
Jay Freeman (saurik): To Erica: While PwnageTool (the god-like tool that lets you make your own firmwares) is commonly used on other devices, it does not yet target the 3G[S] (unless I missed something in the last few days, as I’ve been travelling). So, users don’t really “install jailbroken firmware” on that device. |
|
4:52
|
[Comment From CanonX] How do non-jailbroken users know that they are using your server? |
|
4:53
|
Jay Freeman (saurik): Instead, users using 3.0/3.0.1 are able to use purplera1n or redsn0w to jailbreak their devices. |
|
4:53
|
Jay Freeman (saurik): So, at this time, users who have upgraded to 3.1 (or are purchasing their device with 3.1 out of the box) are unable to jailbreak their devices unless they have a 3.0 signature that they can use to help them downgrade. |
|
4:54
|
Jay Freeman (saurik): To CanonX: I am somewhat confused by the question. You are using my server if you put that line into the hosts file. If you are concerned that you got that process wrong, you might go to “gs.apple.com” in a web browser and see what the response is. |
|
4:55
|
[Comment From Andy] How do you hash SHSHs if Apple stopped signing the files? |
|
4:56
|
Jay Freeman (saurik): To Andy: I do not claim to generate SHSHs for files that Apple is no longer signing. My signature server can only store and “relpay” existing SHSH’s that it has already seen. If you do not have a signature on file with my server for an obsolete firmware (like 3.0), it will not return anything, and iTunes will print a 3002 error. |
|
4:56
|
Jay Freeman (saurik): relpay -> replay |
|
4:56
|
[Comment From Lucas Macedo] I have my iPhone 3G[S] on 3.1, but i have my ECID number. How can I send this to you? Or I can’t send. |
|
4:58
|
Jay Freeman (saurik): To Lucas Macedo: First, to verify, sending me your ECID would not help you downgrade to 3.0, as Apple is no longer signing the 3.0 firmware. However, if you are trying to get your 3.1 signed, currently the only mechanism I have for submitting your ECID is to do a restore using iTunes through my server. |
|
4:59
|
[Comment From j5] Do you plan to reverse engineer the SHSH algorithm using the data you are collecting when your server is used? |
|
4:59
|
Jay Freeman (saurik): I am hoping to have other mechanisms in the future. Although, frankly, spending too much time on this project is not really worthwhile given that the next device will certainly not have the replay bug and possessing signatures for firmwares past 3.2 may not be valuable for many users if no holes are further found. Just spending as much time as I have on this has sometimes felt futile / depressing. :( |
|
4:59
|
Erica: So what you’re saying is that this is really just a stop gap for a little while, yes? |
|
5:00
|
Erica: Let me redirect from these practical questions then for just a few seconds |
|
5:00
|
Jay Freeman (saurik): To j5: The SHSH “algorithm” really comes down to standard public/private key signature encryption technology. One would need either a super computer to mathematically reproduce (or a very awesome thief to steal) the private key from Apple. |
|
5:00
|
Erica: What do you see as the tone of Apple’s moves and where do you see things going. Is this the death knell of jailbreaking? Is it still worth pushing jailbreak forward? |
|
5:01
|
Jay Freeman (saurik): To Erica: Correct. This may continue to provide value for future non-jailbroken users who wish to downgrade their device, but it is only a stopgap measure for users interested in jailbreaking. |
| 5:02 |
Who’s winning
The cat. Apple holds all the cards. ( 6% )
The mouse. The jailbreakers have the ingenuity. ( 20% )
Standoff. No one wins. Everyone loses. ( 15% )
There will always be cats and mice. ( 46% )
Mmmm. Cheeese. ( 13% )
|
|
5:03
|
Jay Freeman (saurik): I am not certain how to respond to that question. Apple is spending time attempting to stop jailbreaking. However, there is a lot of code on devices like this, and small bugs can lead to major exploits. A kernel bug recently found in Linux led to hackers obtaining a root shell on one of the most recently released Android devices, for example: this bug has been latent on Linux systems for many years, and was only found weeks ago. |
|
5:03
|
Megan Lavey: You’ve mentioned the amount of time/energy you’ve put into the project, Jay. How much longer do you see yourself keeping up with this pace? |
|
5:04
|
Megan Lavey: Especially since you are balancing this with full-time graduate studies. |
|
5:04
|
Jay Freeman (saurik): So, it would definitely be premature for myself or anyone else to say that this is a “death knell” for jailbreaking. It should be noted that, as I mostly work on developer tools and software distribution issues, I know relatively little about the actual exploits that people may or may not have in the field. |
|
5:06
|
Jay Freeman (saurik): To Megan: I have actually put a temporary hold on my graduate studies. While UCSB’s “College of Creative Studies” offered an amazing undergraduate education, the “College of Engineering”‘s graduate program and I were not a good fit (if nothing else, I was unable to find a professor during work I found directly interesting). I am currently looking at applying to another school for the 2010 term. |
|
5:07
|
Erica: It sounds to me like the people who most be helped by your service right now are those people who want to downgrade non-jailbroken devices for whatever reason (assuming that Apple does not change the rules again). Is that a fair statement? |
|
5:07
|
Jay Freeman (saurik): (The iPhone Dev Team says “hello” to everyone, and is waving, btw ;P.) |
|
5:08
|
Erica: And we all wave back! |
|
5:09
|
Jay Freeman (saurik): Going forward that is true, but /right now/ the most value is coming to users of 3.1 who have 3.0 signatures on file (there are 50,000 such devices) who are able to maintain their devices (restoring if required being the biggest deal) or downgrade if they accidentally upgraded. |
|
5:10
|
[Comment From Wolfee182] I think Cydia has stored my SHSH on you server. I havent restored in quite a while, because i didnt feel like messing with the jailbreak and getting all my apps the way i want them, But cydia says “This device has a 3.1 ECID SHSH on file.” Is this possible? and how? |
|
5:11
|
Jay Freeman (saurik): To Wolfee182: If you see “This device has a 3.1 ECID SHSH on file.” then that means only what it says: I have a signature on file that would let you restore to 3.1 without asking Apple. At this moment that is not valuable, as Apple themselves will happily sign that revision of the firmware. So, no: you should probably not restore if you want to remain jailbroken (especially as you don’t seem to want to anyway, so I’m not certain why you are asking ;P). |
|
5:12
|
Erica: We’re pretty much running up against the clock right now. We want to thank Jay for spending time with us and being so patient answering all our questions. Thank you everyone who submitted comments, and we’re sorry we couldn’t get to all of your questions. |
|
5:12
|
Erica: We really appreciate you stopping by Jay |
|
5:12
|
[Comment From Stwo] Thanks Jay!! |
|
5:13
|
[Comment From Reverser+] Thanks Jay, keep up the good work! |
|
5:13
|
[Comment From heimbachae] thank you. |
|
5:13
|
[Comment From Deano] Thank you guys |
|
5:13
|
Jay Freeman (saurik): Well, thank you for having me. Hopefully many users have at least a couple less questions regarding the process after this hour spent typing ;P. |
[Via TUAW]
Συζήτηση στο forum: Saurik’s live chat on TUAW
You might also like
More from Cydia
Ο Ηλίας Λιμναίος ξεκλειδώνει το NFC του iPhone! Σύντομα το tweak στο Cydia!
Ο δημοφιλής Έλληνας developer Ηλίας Λιμναίος κατάφερε να ξεκλειδώσει τη δυνατότητα επικοινωνίας του iPhone με NFC συσκευές! Η επικοινωνία κοντινού πεδίου (Near Field Communication, NFC) αποτελεί μια πρότυπη τεχνολογία συνδεσιμότητας, η οποία διαδίδεται και εξελίσσεται ραγδαία με κύριο σκοπό τη λύση αρκετών …
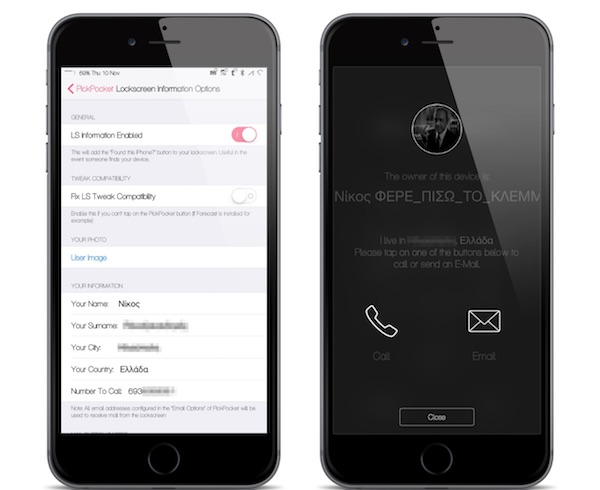
PickPocket: Κορυφαίο “Anti-Theft Tweak” στο Cydia
Ο nikosgnr μας ενημερώνει σχετικά με το PickPocket, ένα νέο Cydia Tweak το οποίο υπόσχεται να προστατέψει την iOS συσκευή σας με τρόπους που η Apple δεν έχει ακόμη (;) προσθέσει στο λειτουργικό της σύστημα: Το PickPocket είναι πλέον ο βασιλιάς των …
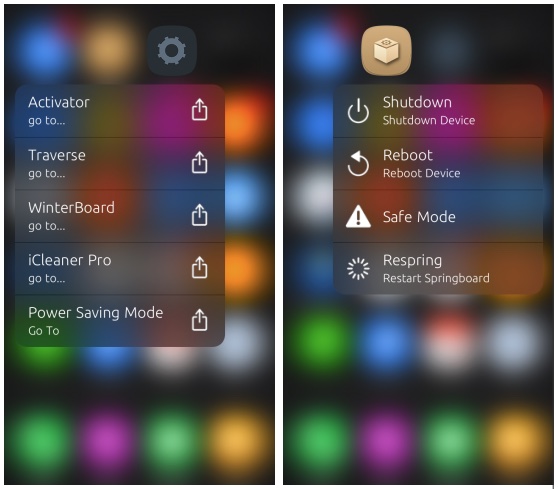
Traverse: Το απόλυτο 3D-Touch menu στο iPhone / iPad σας!
Ο mod vrachamis του iPhoneHellas forum μας ενημερώνει σχετικά το Traverse, ένα πολλά υποσχόμενο tweak που επιτρέπει στον χρήστη να εμπλουτίσει τα αναδυόμενα μενού των εφαρμογών της iOS συσκευής του, με εκατοντάδες επιπλέον επιλογές. Το 3D Touch hardware engine έχει κάνει την εμφάνιση του …
App Admin: Downgrade των εφαρμογών απευθείας απο το App store της συσκευής [Cydia tweak]
Ο mod nikosgnr του iPhoneHellas forum μας ενημερώνει σχετικά με το App Admin, ένα νέο Cydia tweak που μας επιτρέπει να κατεβάσουμε μία πρότερη έκδοση εφαρμογής από αυτήν που διατίθεται αυτή τη στιγμή στο App store... απευθείας από την iOS συσκευή …
To WinterBoard είναι πλέον συμβατό και με το iOS 9
Ευχάριστα νέα για όσους χρήστες Jailbroken συσκευών αρέσκονται στο παραμετροποιούν την εμφάνιση της συσκευής τους, καθώς το WinterBoard αναβαθμίστηκε και πλέον είναι συμβατό και με το iOS 9. Σύμφωνα με τον Saurik, η αναβάθμιση του WinterBoard (v0.9.3919) δοκιμάστηκε από τον ίδιο τον Surenix (γνωστό από …










1 Comment
[…] This post was mentioned on Twitter by iPhone Hellas. iPhone Hellas said: Saurik’s live chat on TUAW: Ο Sauric συμμετείχε στο Live Chat του TUAW και απάντησε σε ερωτήσεις σχετικά με το .. http://bit.ly/k4gMb […]